Why Network Security is Important
A LoneStar Tech Solutions Story
Why Network Security is Important
In an era where businesses rely heavily on digital infrastructure, network security has become one of the most critical components of organizational success. From protecting sensitive customer data to ensuring business continuity, robust network security measures are no longer optional—they're essential.
The Growing Threat Landscape
Cyber threats are evolving at an unprecedented pace. According to recent studies, cyberattacks occur every 39 seconds, with businesses of all sizes becoming targets. These threats include:
- Ransomware attacks that can cripple operations and demand substantial payments
- Phishing scams designed to steal credentials and sensitive information
- DDoS attacks that overwhelm systems and disrupt services
- Insider threats from compromised or malicious employees
- Advanced persistent threats (APTs) that silently infiltrate networks over extended periods
The Cost of Security Breaches
The financial impact of a security breach extends far beyond immediate remediation costs:
Direct Costs
- Emergency response and incident management
- Legal fees and regulatory fines
- System restoration and data recovery
- Enhanced security measures post-breach
Indirect Costs
- Lost revenue during downtime
- Damaged reputation and customer trust
- Decreased employee productivity
- Loss of competitive advantage
- Long-term business impact
According to IBM's Cost of a Data Breach Report, the average cost of a data breach in 2024 exceeded $4.45 million—a figure that can be devastating for small to medium-sized businesses.
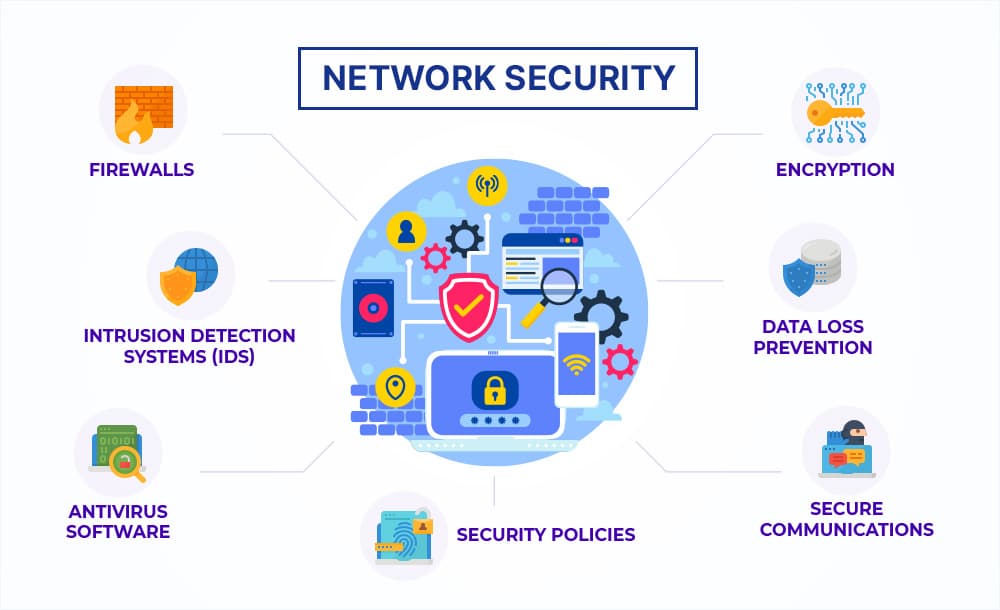
Key Components of Network Security
Effective network security requires a multi-layered approach:
1. Firewall Protection
Modern next-generation firewalls provide the first line of defense, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules.
2. Intrusion Detection and Prevention
IDS/IPS systems continuously monitor network traffic for suspicious activity and can automatically block potential threats.
3. Secure Access Controls
Implementing robust authentication mechanisms, including multi-factor authentication (MFA), ensures that only authorized users can access sensitive systems and data.
4. Encryption
Data encryption protects information both in transit and at rest, rendering it useless to unauthorized parties even if intercepted.
5. Regular Security Audits
Periodic vulnerability assessments and penetration testing help identify weaknesses before attackers can exploit them.
6. Employee Training
Human error remains one of the largest security vulnerabilities. Regular security awareness training helps employees recognize and respond appropriately to threats.
Regulatory Compliance Requirements
Many industries face strict regulatory requirements regarding network security:
- HIPAA for healthcare organizations
- PCI DSS for businesses handling credit card transactions
- GDPR for companies processing EU residents' data
- SOX for publicly traded companies
- CMMC for defense contractors
Non-compliance can result in severe penalties, legal consequences, and loss of business licenses.
The Business Benefits of Strong Network Security
Beyond risk mitigation, robust network security delivers tangible business advantages:
Enhanced Customer Trust
Customers are increasingly aware of data privacy concerns. Demonstrating strong security practices builds trust and can be a competitive differentiator.
Improved Operational Efficiency
Secure, stable networks experience fewer disruptions, enabling employees to work productively without security-related interruptions.
Business Continuity
Effective security measures ensure that critical business operations can continue even in the face of cyber threats or attacks.
Competitive Advantage
Many enterprise clients require vendors to meet specific security standards. Strong network security can open doors to new business opportunities.
Best Practices for Network Security
Organizations should implement these fundamental practices:
- Adopt a Zero Trust Architecture: Never trust, always verify—even for internal network traffic
- Implement Network Segmentation: Divide your network into segments to contain potential breaches
- Maintain Updated Systems: Regular patching and updates close known vulnerabilities
- Monitor Continuously: 24/7 network monitoring enables rapid threat detection and response
- Develop an Incident Response Plan: Prepare for potential breaches with documented procedures
- Backup Critical Data: Regular, secure backups ensure business continuity
- Control Access Privileges: Follow the principle of least privilege
The Role of Managed Security Services
For many organizations, maintaining comprehensive network security in-house is challenging due to:
- The shortage of qualified cybersecurity professionals
- The complexity of modern threat landscapes
- The need for 24/7 monitoring and response
- Rapidly evolving technologies and attack vectors
Managed Security Service Providers (MSSPs) offer expertise, advanced tools, and continuous monitoring that many businesses cannot achieve independently.
Looking Ahead: Emerging Security Trends
The network security landscape continues to evolve:
- AI and Machine Learning: Advanced threat detection and automated response capabilities
- Cloud Security: Protecting data and applications in hybrid and multi-cloud environments
- IoT Security: Securing the expanding attack surface from connected devices
- Zero Trust Network Access (ZTNA): Moving beyond traditional perimeter-based security
Conclusion
Network security is not a one-time investment but an ongoing commitment to protecting your organization's most valuable assets—its data, reputation, and ability to operate. As cyber threats grow more sophisticated, businesses must prioritize network security as a fundamental component of their overall business strategy.
The question is no longer whether you can afford to invest in network security, but whether you can afford not to. The cost of prevention is invariably lower than the cost of recovery from a breach.
Need help securing your network infrastructure? LoneStar Tech Solutions LLC provides comprehensive network security solutions tailored to your business needs. Contact us today for a free security assessment.